

النظرة الاستراتيجية
Strategic Vision
دوافع المشروع
The Why
الأهداف الرئيسية
Key Benefits
الخدمات المقدّمة
Service Offering
آلية العمل
How Does it Work?

DDos Hybrid Service Protection
1822
- 28
3362
- 108
2991
- 109
Help AG Cyber Defense Center Trend

13m
MTTA
(ack)
31m
MTTR
(respond)
36m
MTTR
(resolve)

11m
33m
46m
Threats by Geolocation
Alert Trend - SIEM, EDR, NDR, UEBA
19
Critical
286
High
404
Medium
711
Low/ Staging
Top Digital Risks
64
Credential Theft
21
Data Leakage
13
Brand Abuse
95
Phishing
Alert Mapped with Cyber Kill Chain - MSTD
Top Alerts by Industries
Banking
601
3%

Healthcare
71
27

Government
430
3%

MITRE Technique use case deployed - TCR
Initial Access
18
Execution
25
Percistence
30
Privilege Escalation
60
Defence Evasion
20
Credential Access
50
Discovery
18
Lateral Movement
23
Collection
72
Command and Control
48
Exfiltration
38
Impact
28
Dubai Cyber Index
0
1
2
3
4
5
98%
Response Time Index
Resolved Incident %
Automated use case Pipeline Status
7
14
15
20
9
Digital Risk Rating by Customer



Strategic Vision / النظرة الاستراتيجية
تحقيق أعلى مستوى من الكفاءة في الأمن السيبراني
Achieve the Highest Level of Cybersecurity Excellence
حماية البيانات الحيوية والأصول
الرقمية
Safeguard Critical Data and Digital Assets
رصد التهديدات والتعامل معها بشكل استباقي
Proactive Threat Detection and Response



Top Digital Risks / أهم المخاطر الرقمية
في عام 2023، تم تسجيل ما يقرب من 30,000 من التنبيهات عالية الخطورة، كانت النسبة الأكبر تعود إلى سرقة البيانات (49%) وإساءة استخدام العلامة التجارية (39%) كأهم حالات الاستخدام
In 2023, Of nearly 30,000 critical risk alerts identified, the dominant percentage were attributed to Credential Theft (49%) and Brand Abuse (39%) as top use cases.



UAE's Cyber Threat Landscape / التهديدات السيبرانية في الإمارات العربية المتحدة
هجمات الفدية
Ransomware
لا تزال هجمات الفدية تشكل الخطر الأكبر حيث يزداد تركيز مجموعات الاختراق العالمية على المنطقة، تشكل هجمات الفدية ما نسبته 51% من مجموع الاختراقات المسجلة في الدولة.
Ransomware attacks remain the biggest threat as global hacking groups increasingly focus on the region, with ransomware attacks accounting for 51% of all breaches recorded in the country.
خسائر اختراق البيانات
Data breach losses
| Year | Global | Middle East |
| 2022 | 4.35 | 7.46 |
| 2023 | 4.45 | 8.07 |
| 2024 | 4.88 | 8.57 |
- In million U.S. dollars
- 2024 prediction
هجمات تعطيل الخدمة
DDoS Attacks
| DDoS Attacks targeting UAE: | |
| 2022 | 150,204 |
| 2023 | 213,434 |
| 2024 | 266,512 |
- 2024 prediction
- 2024 (Q1) : 66,628



Top Cyber Attacks / أهم الهجمات السيبرانية
Ransomware Attacks
Social Engineering and Phishing
Cloud Security Breaches
Identity & Data Theft
Nation State Attacks (Advanced Persistent Threats)
DDoS Attacks



How Does it Work?
Technology
The SOC relies on a suite of advanced tools and technologies, such as SIEM (Security Information and Event Management) systems, intrusion detection systems, and threat intelligence platforms and etc.. These technologies help the team to automate tasks, detect threats, and gain insights into organization's security posture.
People
The SOC team consists of skilled security analysts and incident responders who monitor, detect, and manage security incidents. They bring expertise to identify threats, analyze risks, and coordinate responses to protect the organization.
Process
Standardized procedures guide how the SOC operates, ensuring a consistent approach to threat detection, incident response, and recovery. This includes everything from alert handling to incident escalation and reporting.



SOC Team
Threat Intelligence Analysis Team
Collects and analyzes data on emerging threats to inform and improve defenses
Digital Forensics and Incident Response (DFIR) Team
Investigates security breaches, performs forensic analysis, and recovers critical data.
SOC Manager
Oversees SOC operations, ensuring security processes and policies are followed effectively

Red Team
Conducts simulated attacks to test and strengthen the organization's defenses
Compliance & Governance
Manages audits, ensures compliance, and aligns security with governance frameworks
Security Analysts
Monitors and detects security threats and events as the frontline of SOC defense



Main Process
SOC Framework
To manage and improve the security operations. It outlines the tools, processes, people, and strategies required to detect, prevent, respond to, and recover from cybersecurity incidents.
Detection Engineering Process
This process focuses on designing and improving detection mechanisms to identify threats within the network or systems.
Framework
Monitoring
Detection
Incident
Security Logging and Monitoring Process
This process involves collecting, storing, analyzing, and monitoring security logs to detect suspicious or malicious activity.
Incident Management Process
This process is responsible for handling security incidents, minimizing damage, and restoring normal operations.



How Does it Work
Identity
Endpoint & Servers
Network
Data
Cloud
Application
Monitor
Detect
Response
Analyze
Identity
Endpoint & Servers
Network
Data
Cloud
Application
Log Management
Threat Intelligence
User Behavior Analytics
Threat Hunting
Network Analytics
Incident Management
Orchestration, Automation, and Response



High Level Architecture

People
Process
Threat intelligence
ASRM
Secure Internet Access
XDR
CTEM
Cloud Security
Intra VM firewall
Micro segmentation
Application security
Static file analysis
Email security
SIEM
Cloud SIEM
UEBA
SOAR automation
Vulnerability assessment
PAM
Network layer IPS
Active Directory Security
EPP
Workloads protection
Application visibility
Perimeter Firewall
Core Firewall
WAF
Sandbox



Key Benefits / الفوائد الرئيسية
الكشف الاستباقي عن التهديدات
Early Threat Detection
سرعة الاستجابة
Rapid Response
تحليل التهديدات باستخدام الذكاء الاصطناعي
Threat Analysis Powered by AI
حماية البيانات الحساسة
Protection of Sensitive Data
الالتزام باللوائح والقوانين
Compliance With Regulations



Why AjmanOne SOC?
2 Billion+
الأحداث الأمنية التي تمت معالجتها وتحليلها
Security events processed and analyzed per month
1500+
حالات استخدام أمنية مُطبقة لإنشاء تنبيهات أمنية
Security Use cases deployed to generate Security notables
2,000+
التنبيهات الأمنية والطلبات التي يتم حلها شهرياً
Security Alerts and requests handled per month
120+
عدد النصائح الأمنية التي تم نشرها
Threat advisories created, published and released
50+
عدد عمليات التصيد التي تم تنفيذها
IOC Driven Threat Hunts performed
100+
عدد الحوادث الأمنية التي تم التعامل معها شهرياً
Potential incidents handled per month



Service Offerings / الخدمات المقدّمة
Detection & Response
Threat Intelligence
Digital Forensics & Incident Response
SOC Engineering & VA Assessment
PT & Red Teaming
- 24/7 Monitoring
- Threat Hunting
- Incident Response
- Predictability
- Early Detection
- Intelligence -Driven Hunting
- Call In Case Of Incident
- Support During Recovery
- Use case creation
- Technology fine tunning
- Vulnerability management
- Validation of environmental capability to predict, detect, respond and recover from the incident
- Vulnerability Exposure
- Config + Control
- Threat Activity



Risk Overview
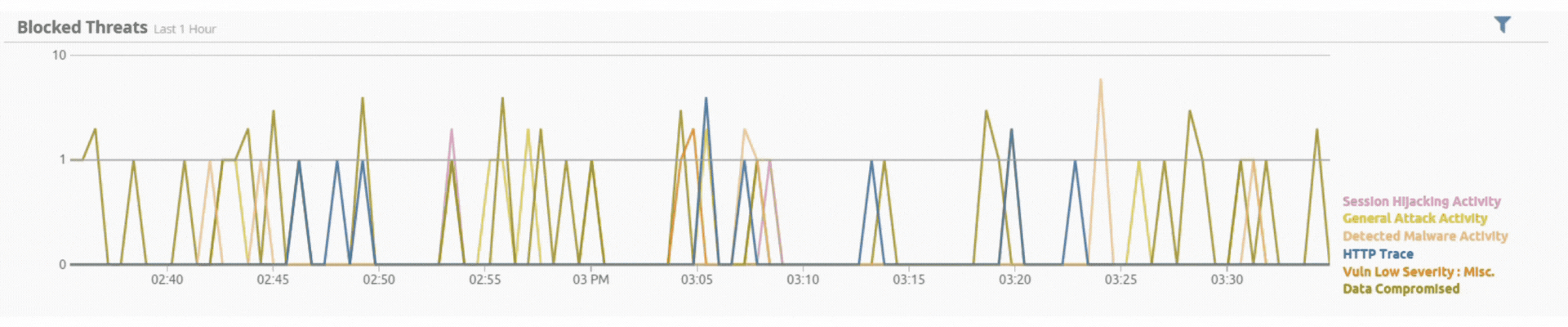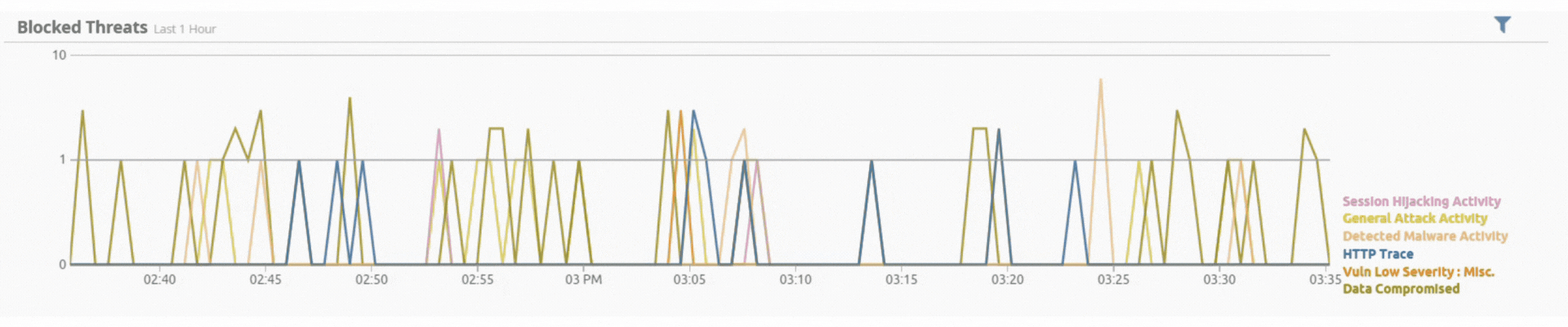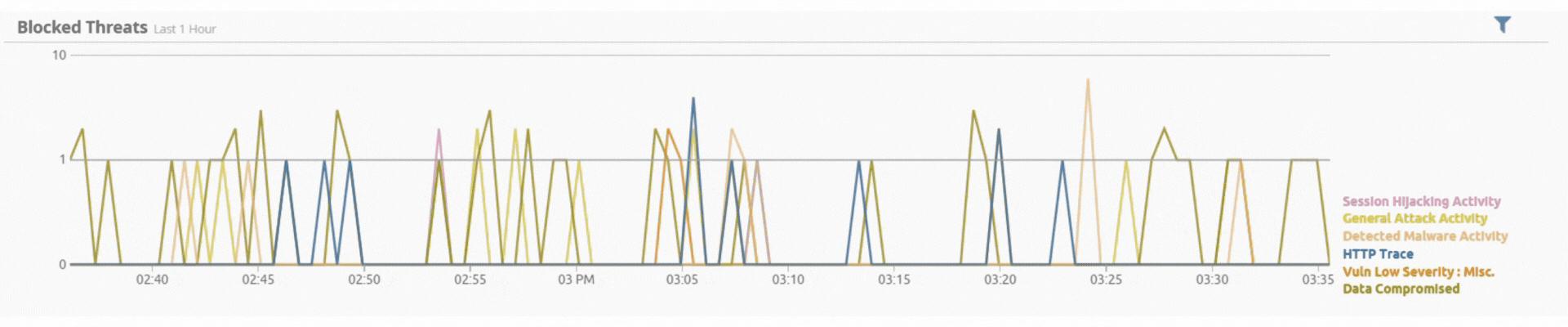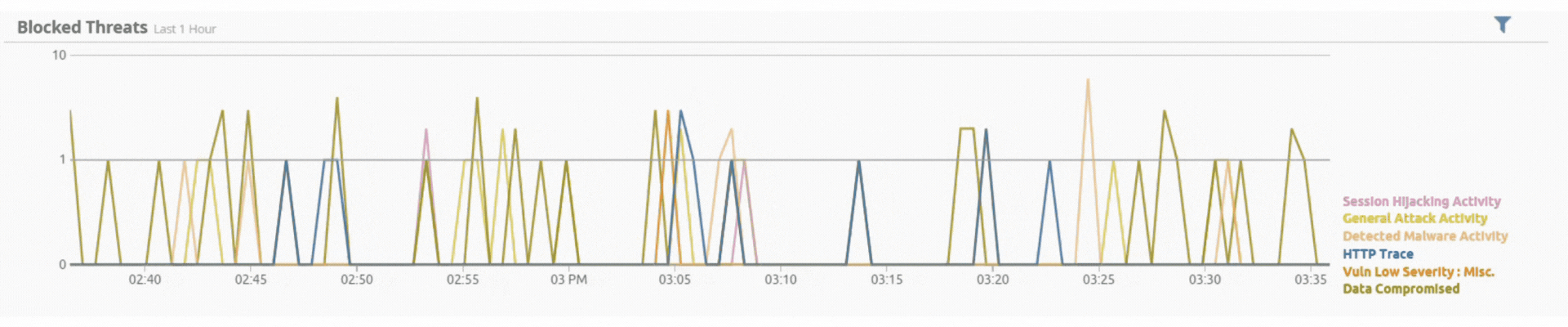
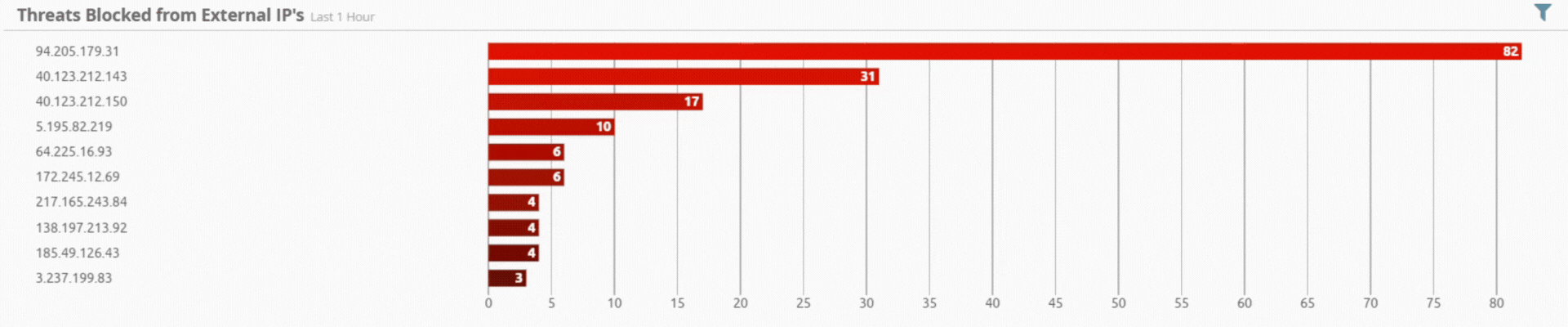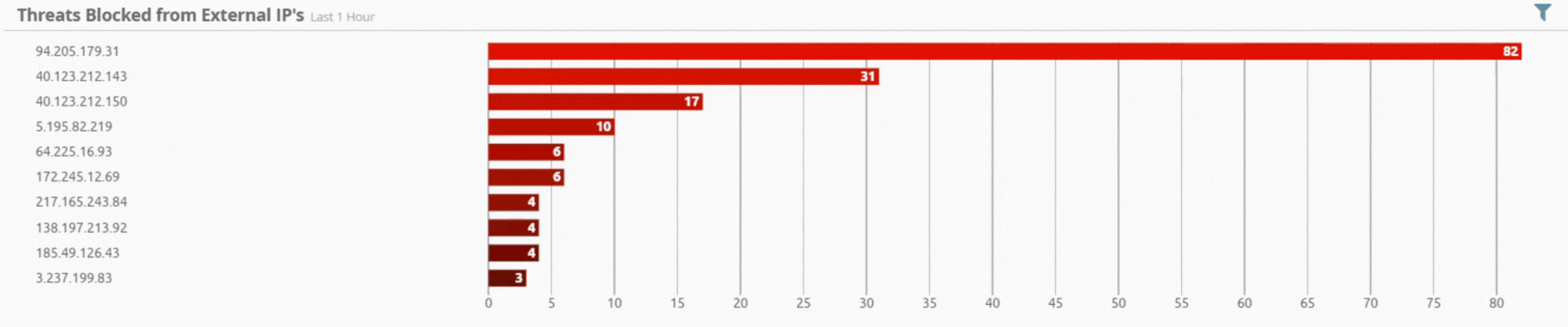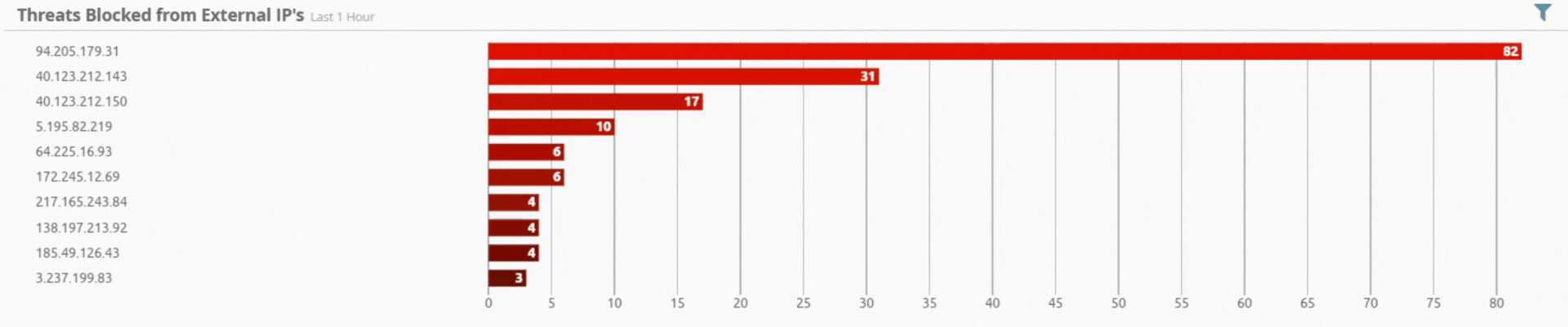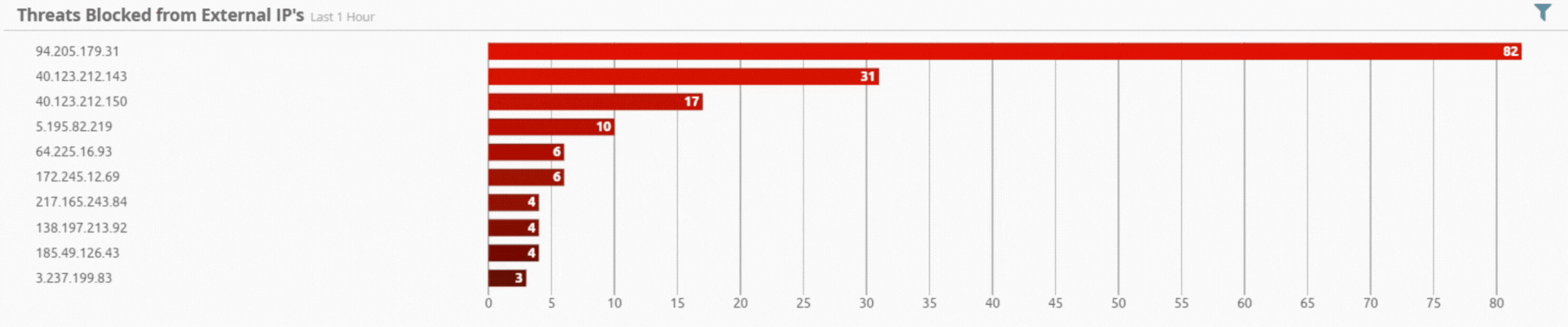
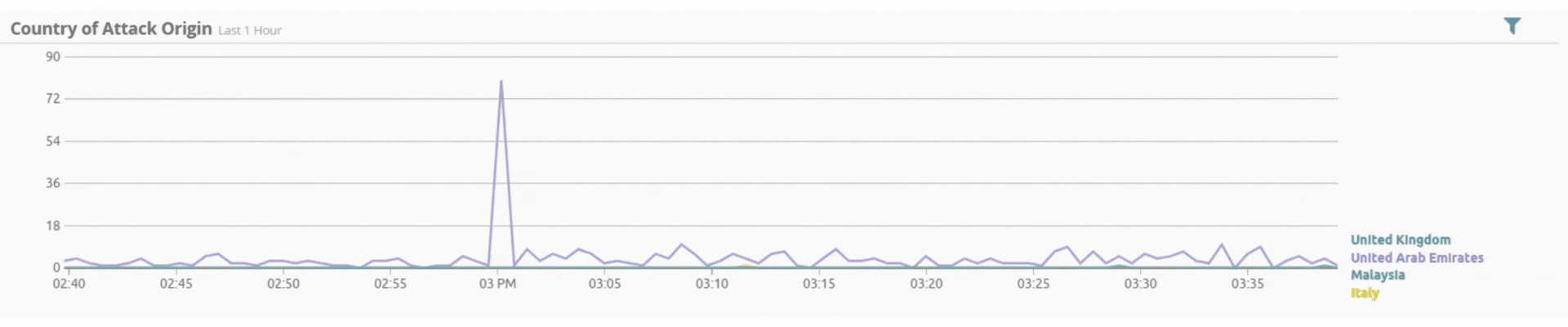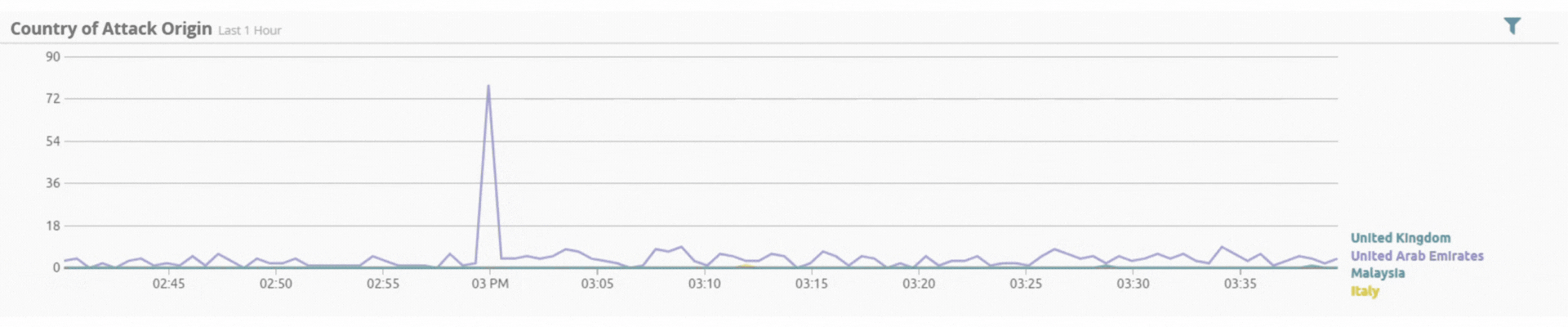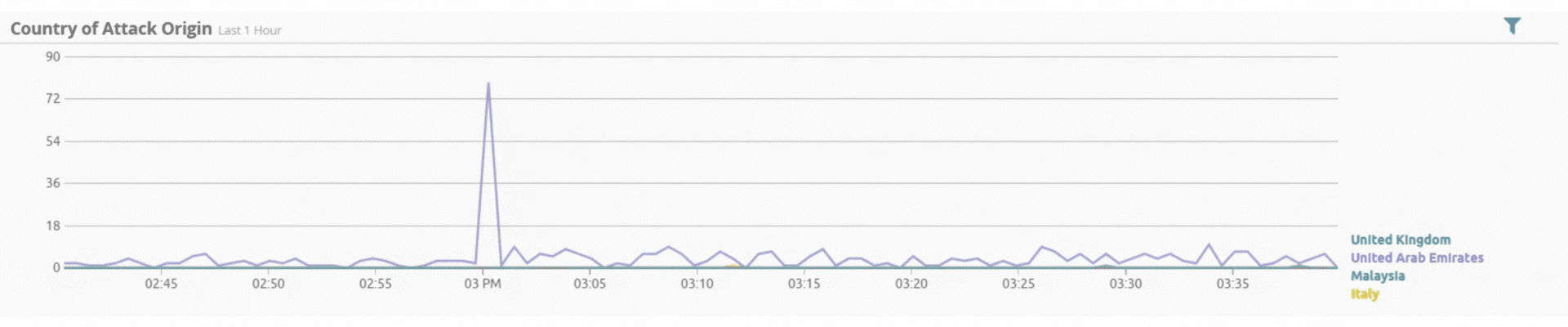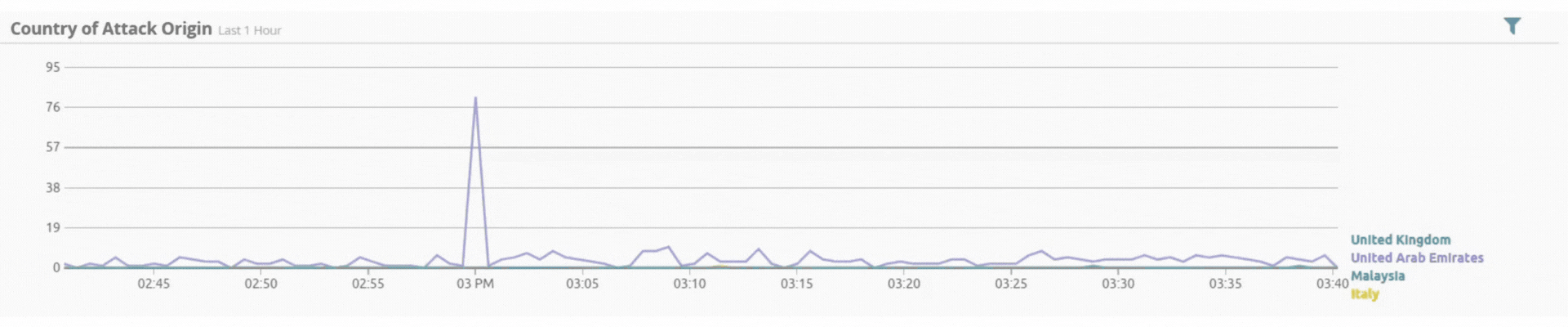
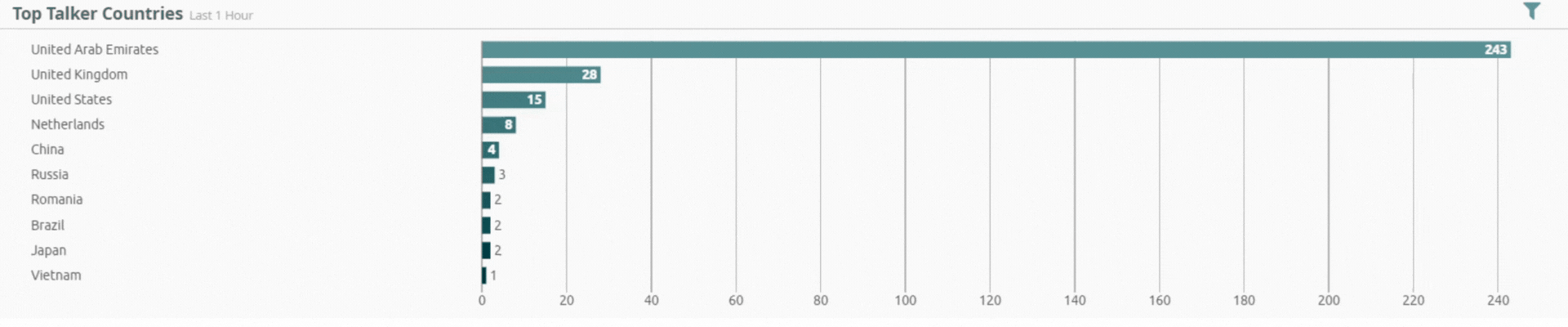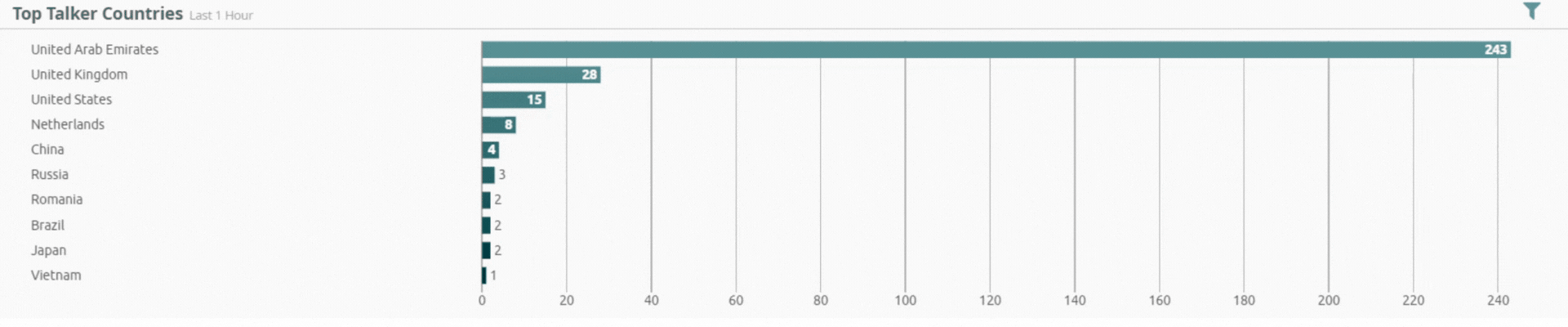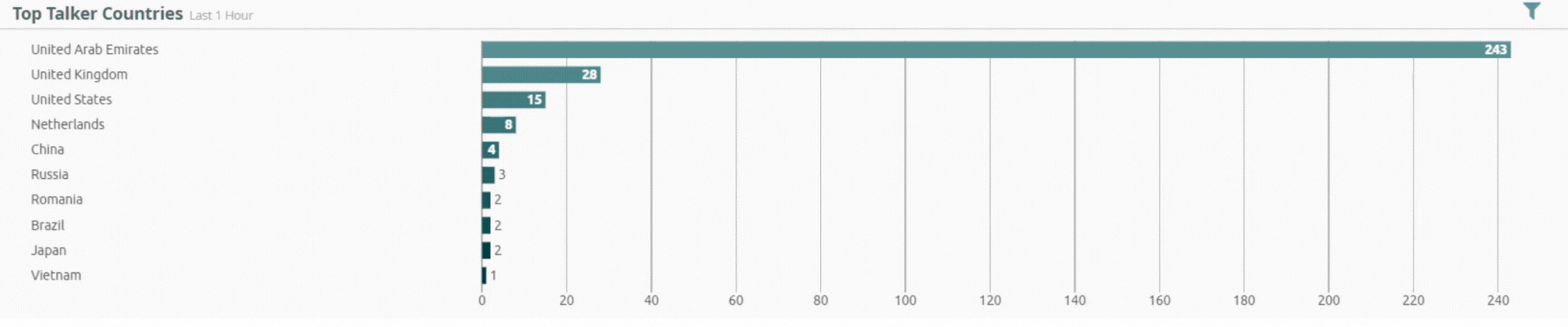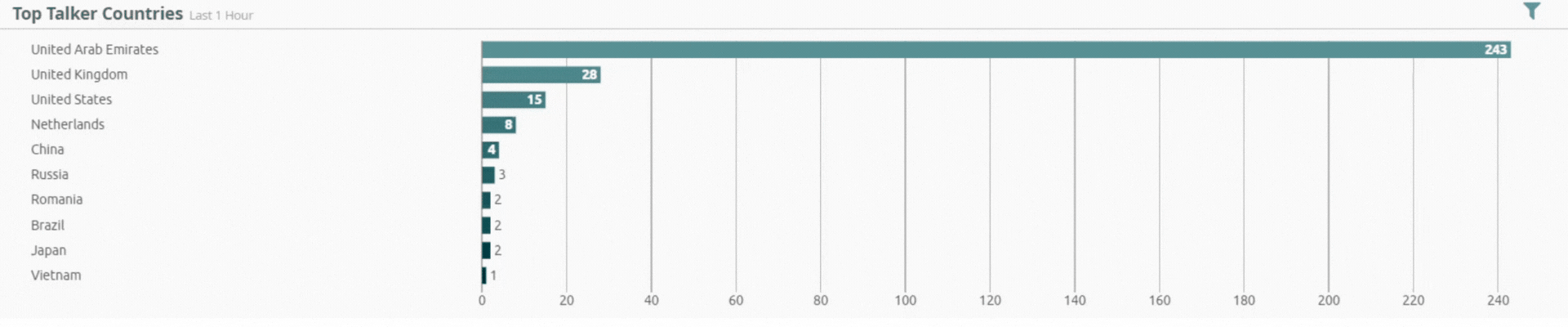
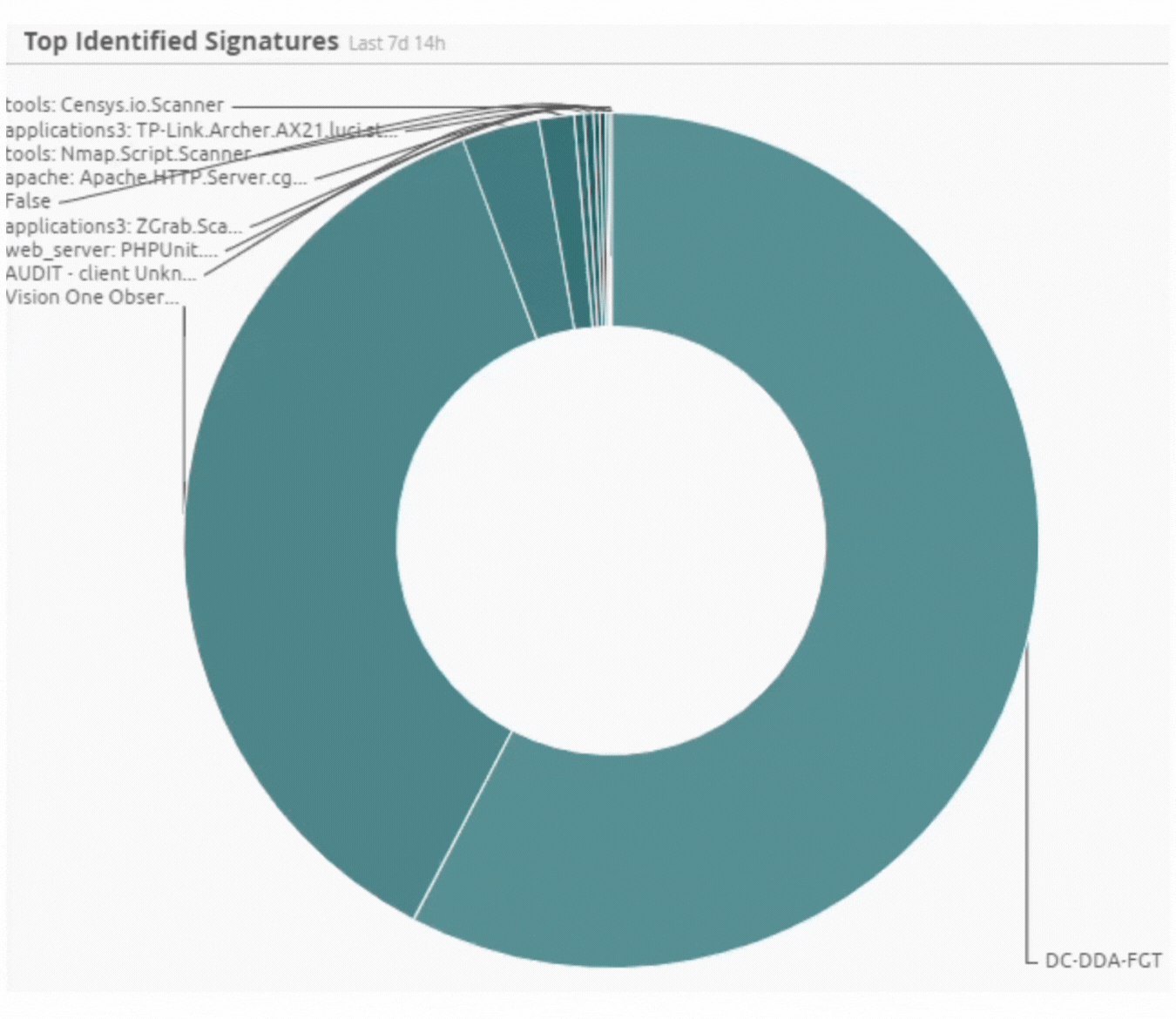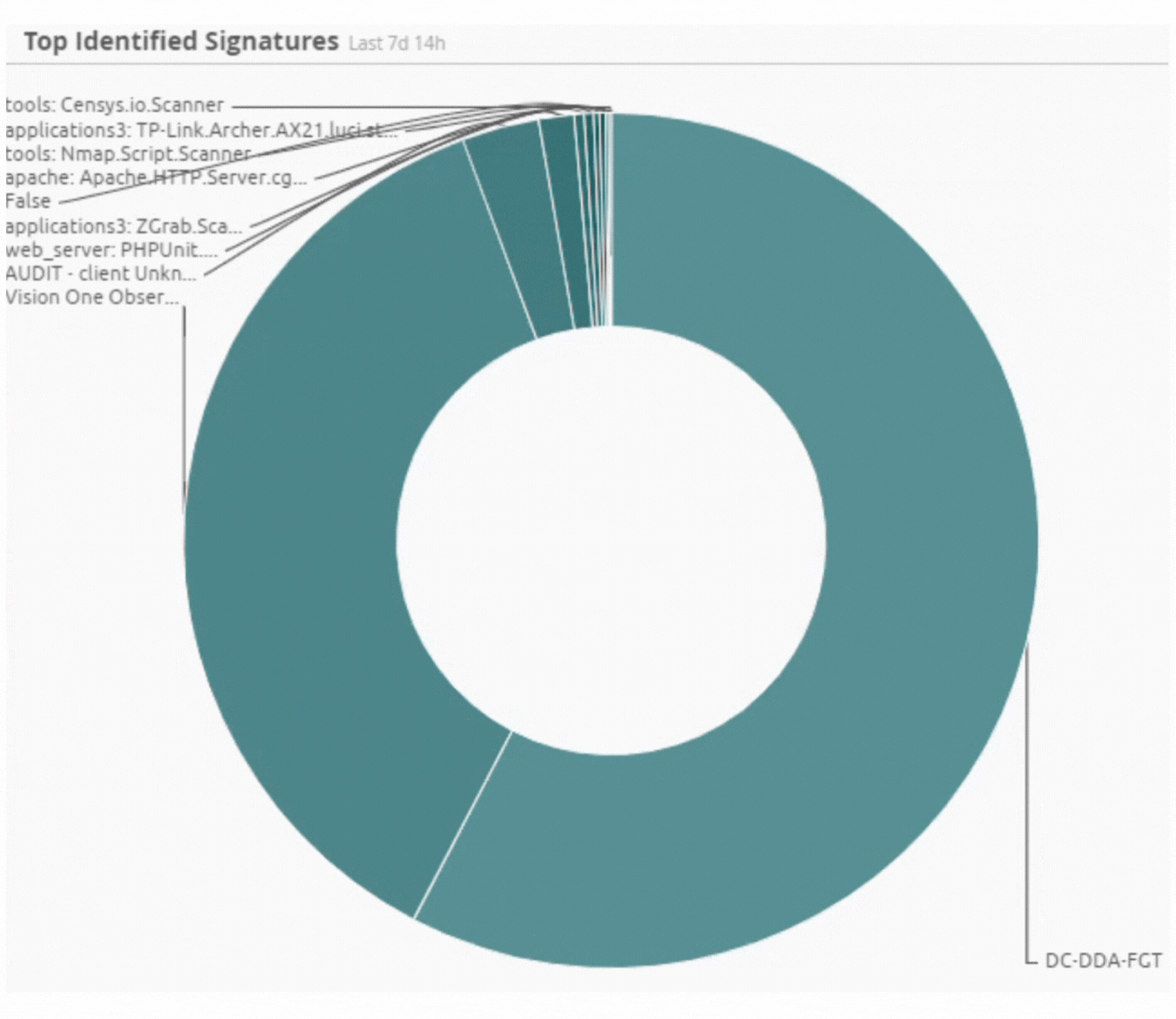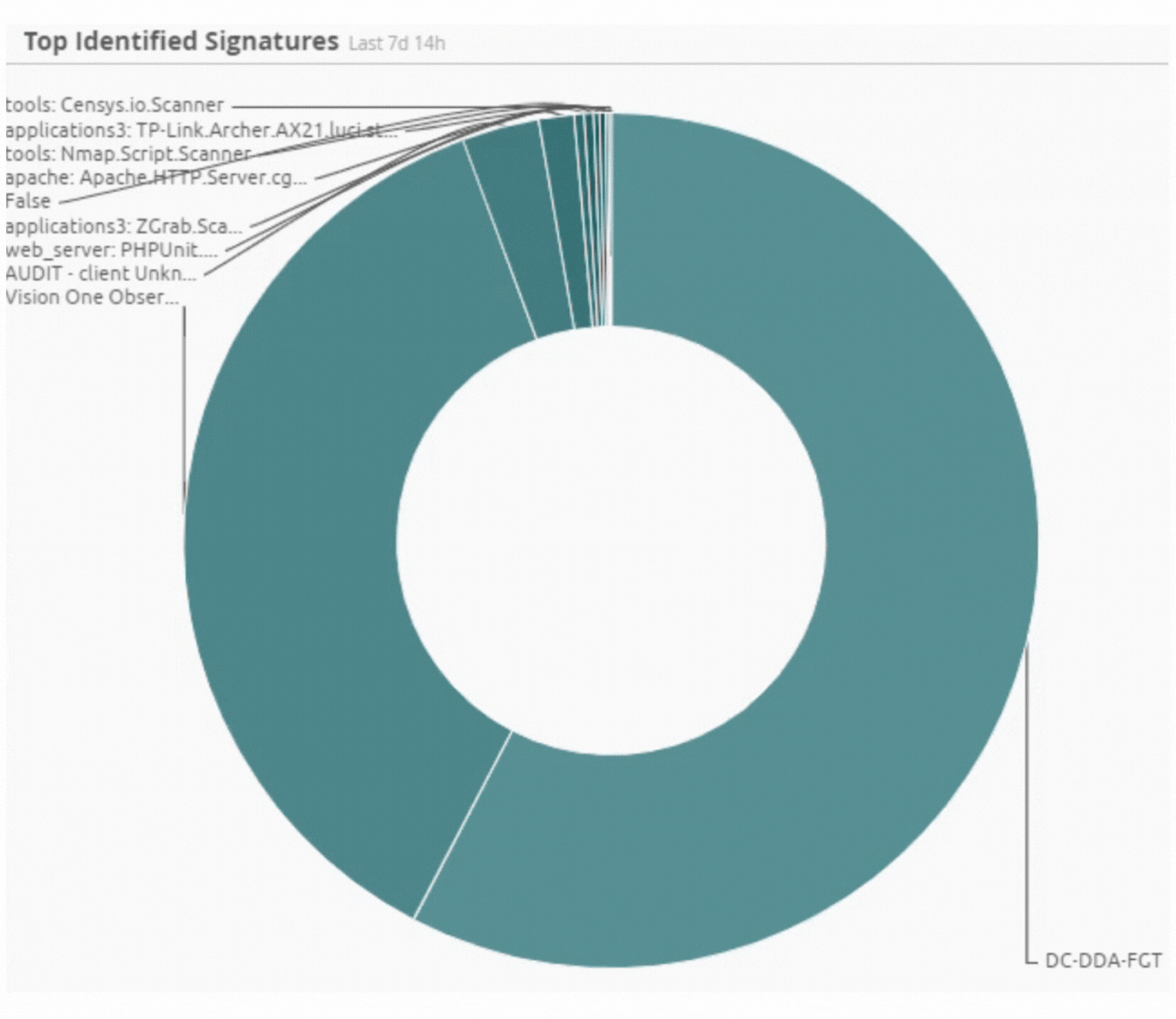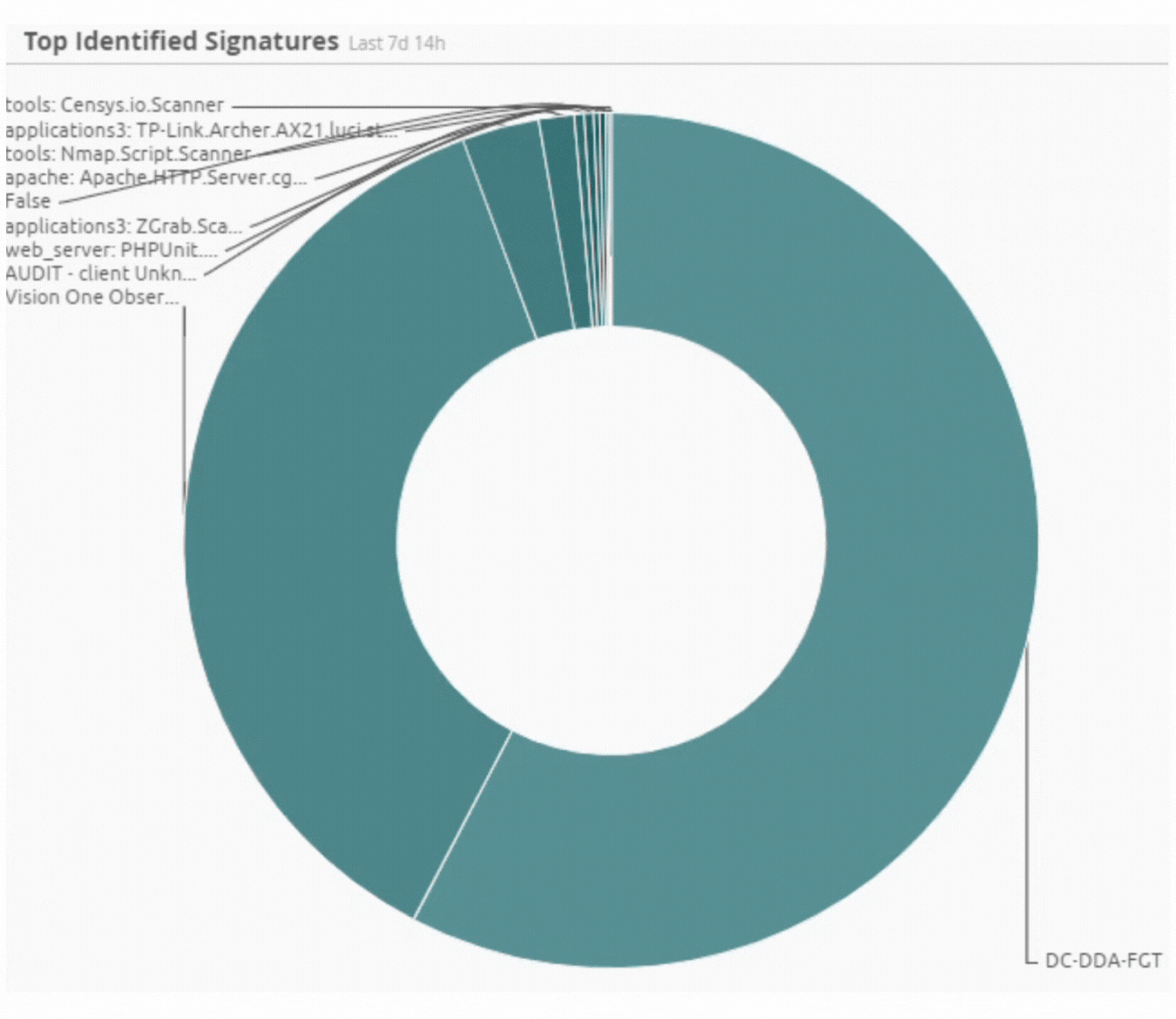
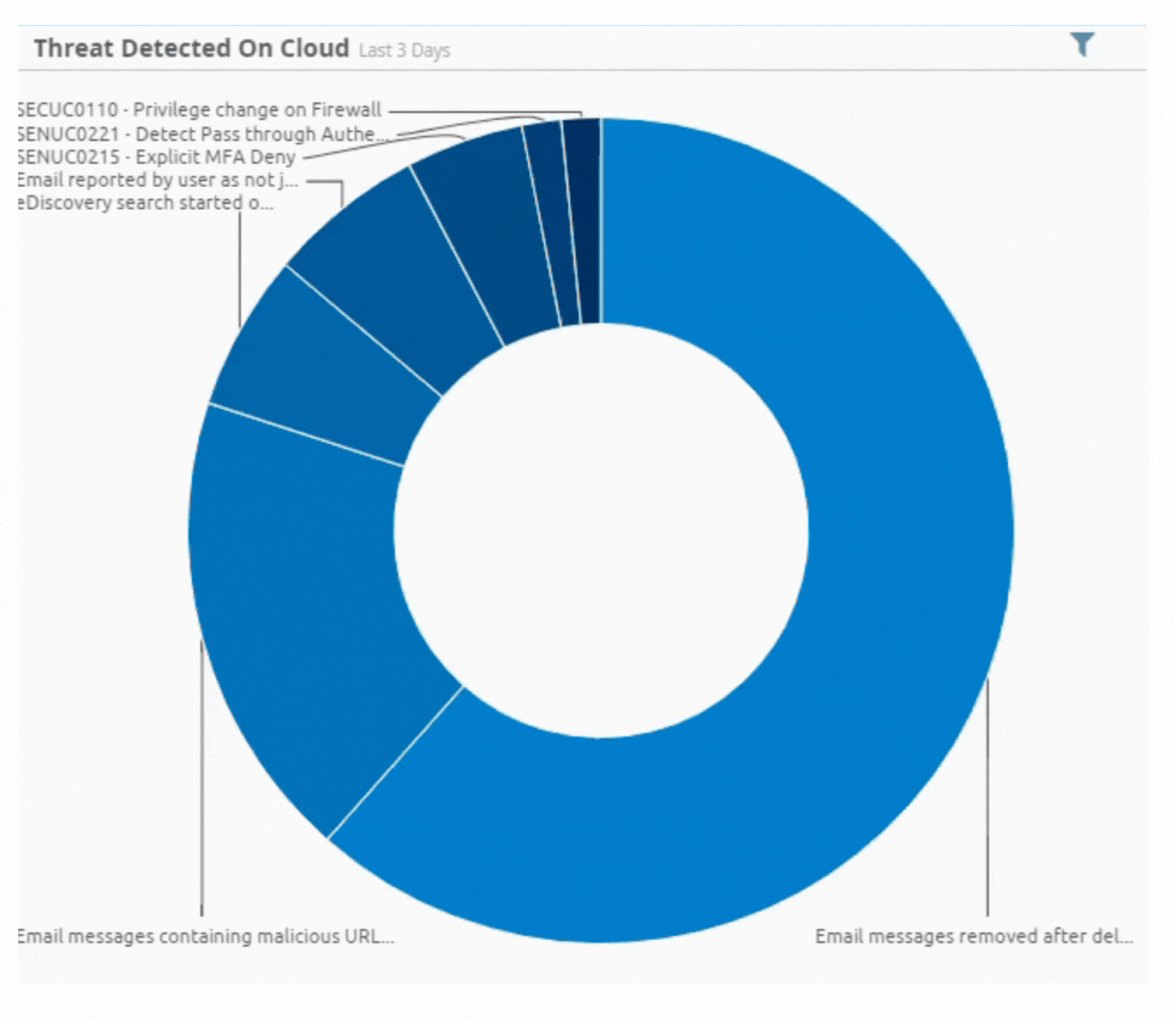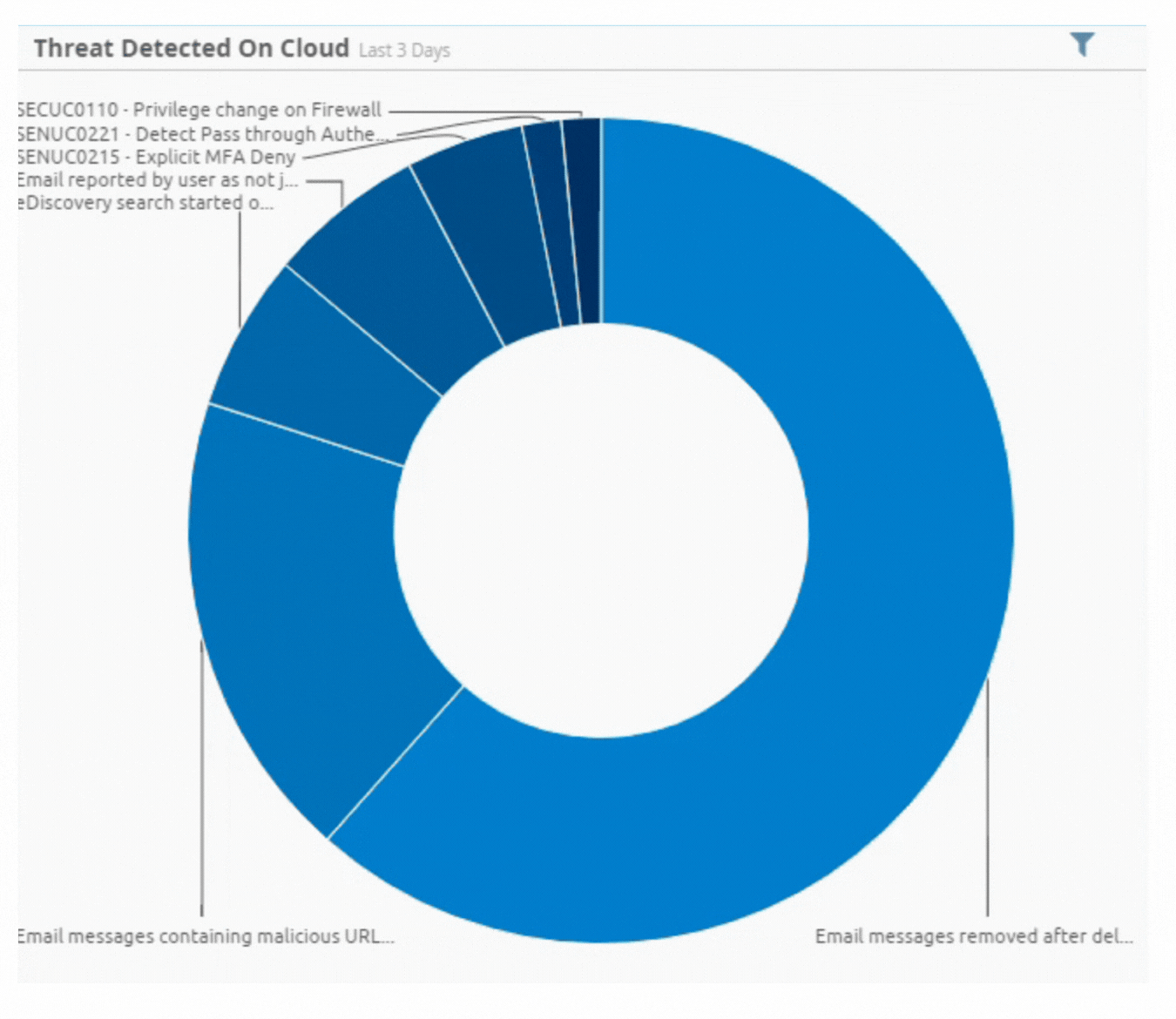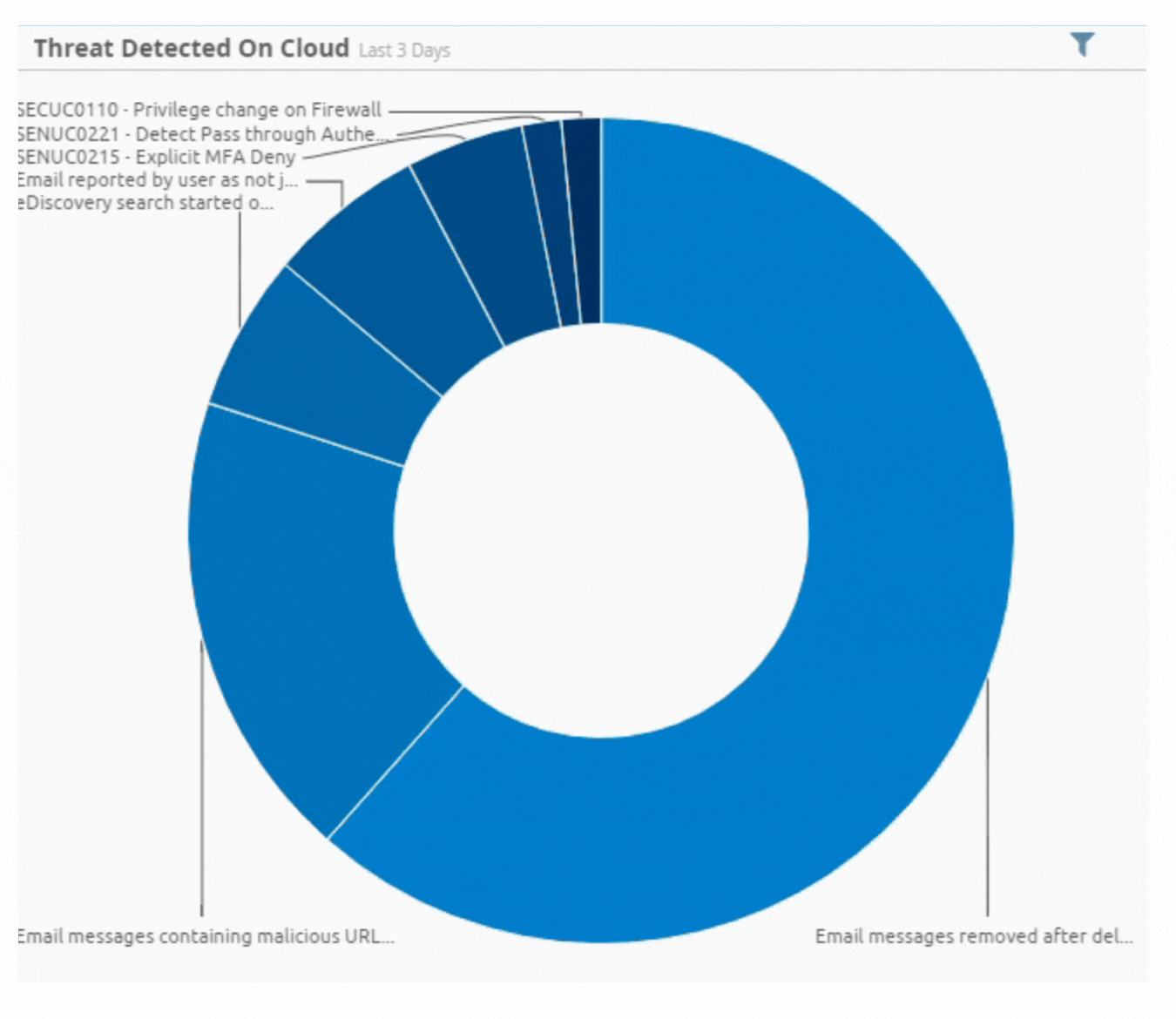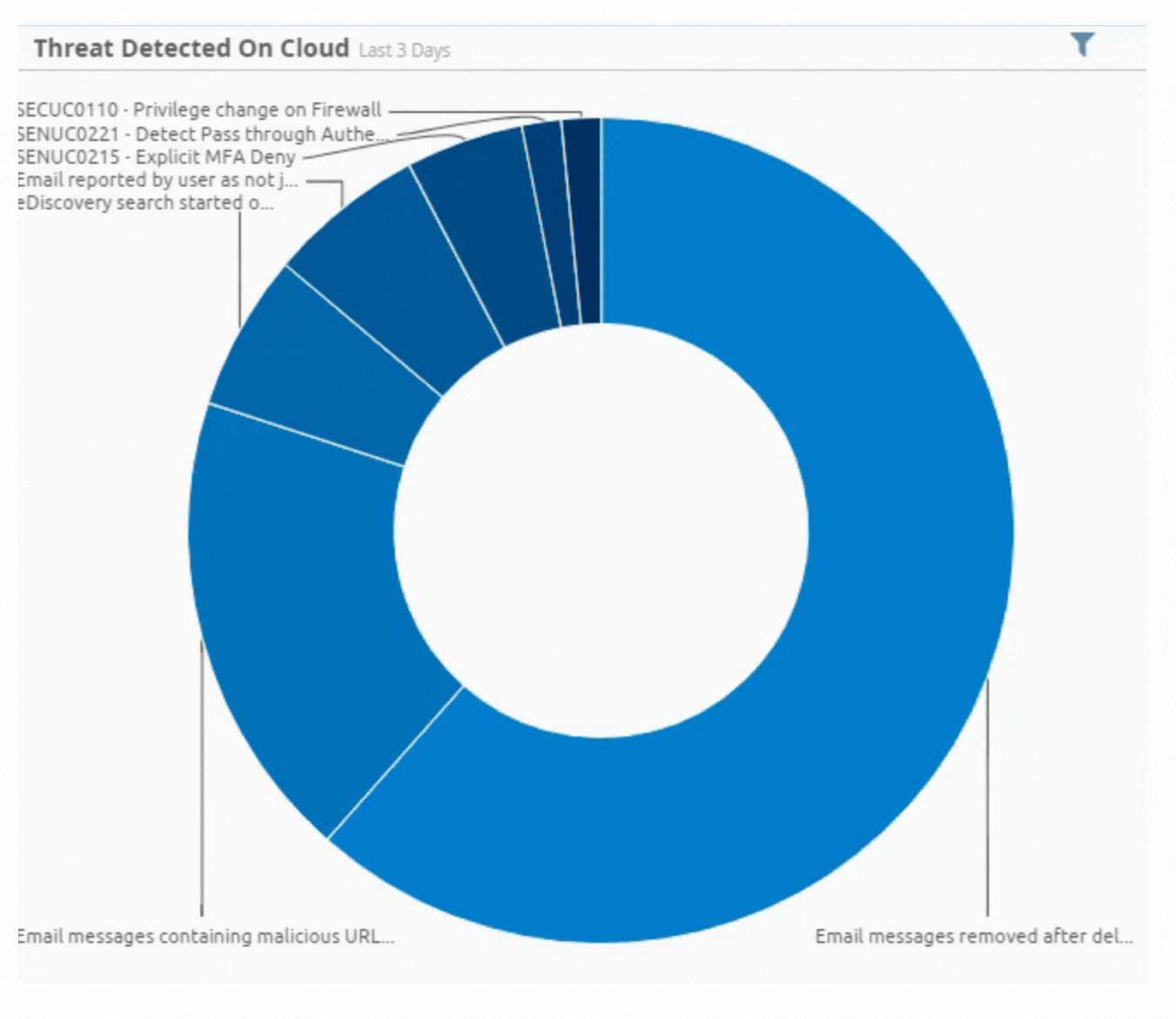
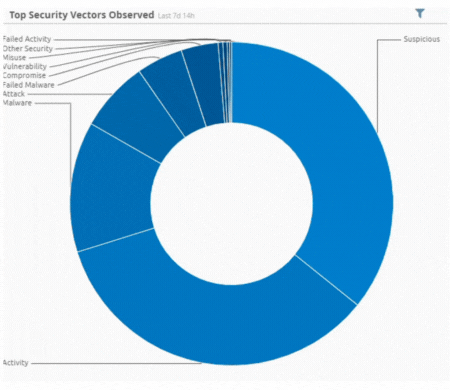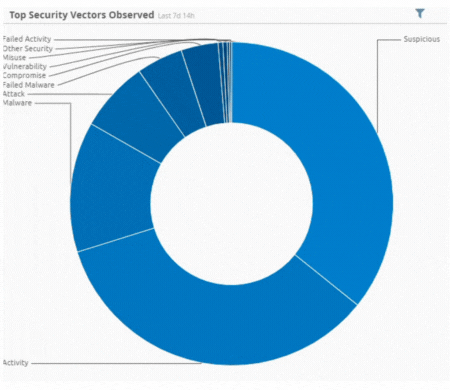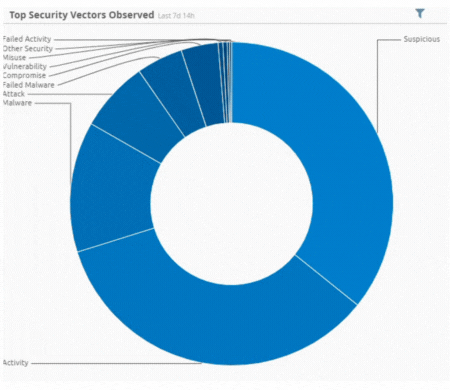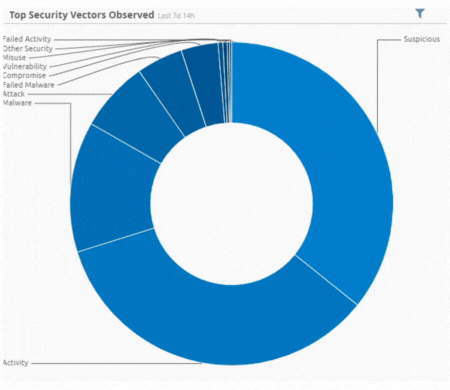



Incident by Sector - UAE only
2023
2022

